None of these installers enable Fargate Runtime Threat Detection. For this feature, it is required to follow a different installation method (covered in Module 4.3).
Module 1: Install
After authenticating your new Sysdig account, the onboarding wizard screen will be shown.
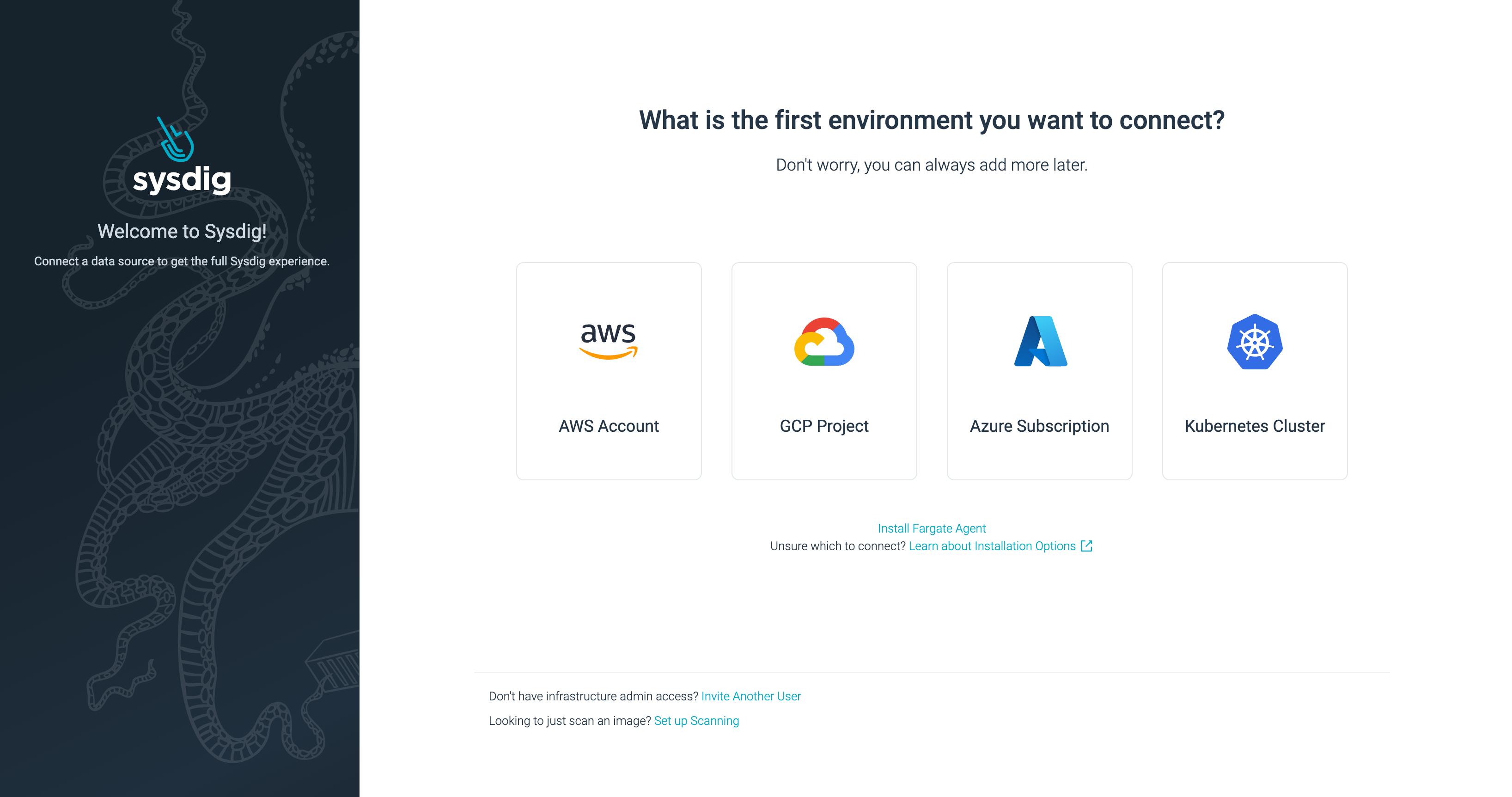
Onboarding wizard.
Choose “AWS Account” to start.
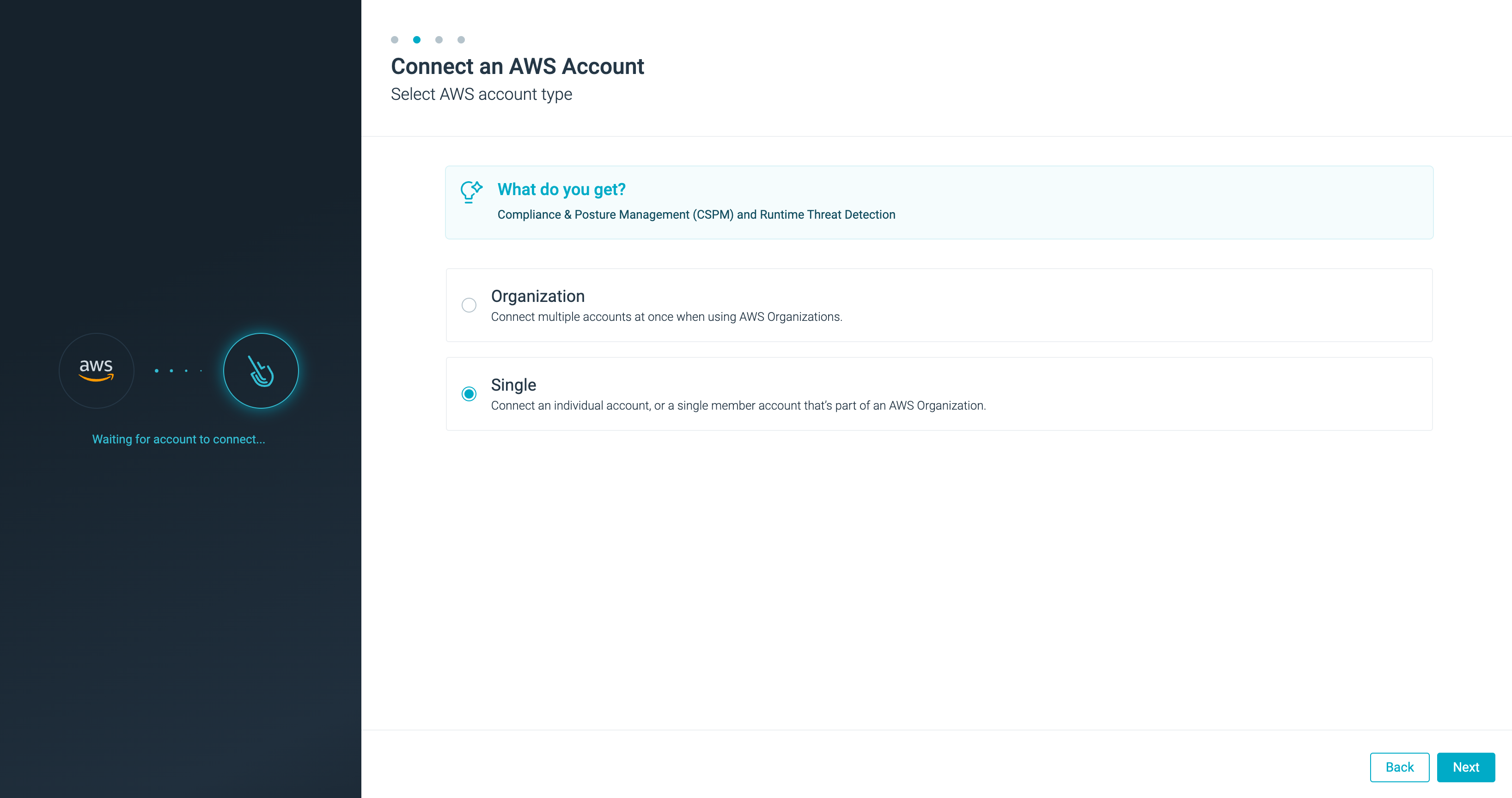
Onboarding type.
Choose “Single” for this workshop.
In this first section you will learn:
How to deploy Sysdig Secure for Cloud. There are two alternative methods:
How to deploy the Sysdig Agents with Helm in an EKS Cluster. There are multiple methods to install a Sysdig Agent that are not covered in this workshop.
For the Cloud installers (Terraform and CloudFormation) choose just one of the available methods to continue with this workshop. Following one or the other depends on the user preferences and previous experience with each of the tools.
Features enabled by each installer
The Sysdig Secure for Cloud installer will enable all the next Sysdig Secure Cloud features:
- Posture and compliance (CSPM)
- CIEM
- Cloud Threat detection using EventBridge
- Vulnerability Management
The deployment of the Sysdig Agents in an EKS cluster, enable most of the Sysdig Monitor and Secure features. In the particular context of this training, the agents are required to enable:
- Runtime Threat Detection in EKS
- ECR image scanning
- KSPM: Actionable Compliance and IaC Remediation
- Kubernetes Admission Controller for cluster Audit logging in EKS