Push and Scan images on ECR
Download Example Dockerfile and Sources
Now that our automated scanner is in place, it will trigger full registry scans every so often.
- Lets trigger a manual scan (we don’t want to wait until the cron job triggers the next scan). Launch a job instance using kubectl.
kubectl create job --from=cronjob/registry-scanner registry-scanner-manual
The job should create a pod in the default namespace to retrieve the list of images and scan them one by one. Logs from the pod can be checked to see if everything went fine.
kubectl get po
Take note of the pod name, it shoul dbe something like registry-scanner-manual-string. Retrieve pod logs with the appropriate pod name.
kubectl logs registry-scanner-manual-lncqq
See Scan Results on Sysdig Secure Dashboard
To see the scan results on Sysdig Secure Dashboard,
Log into the Sysdig Secure UI, and browse to Vulnerabilities > Registry:
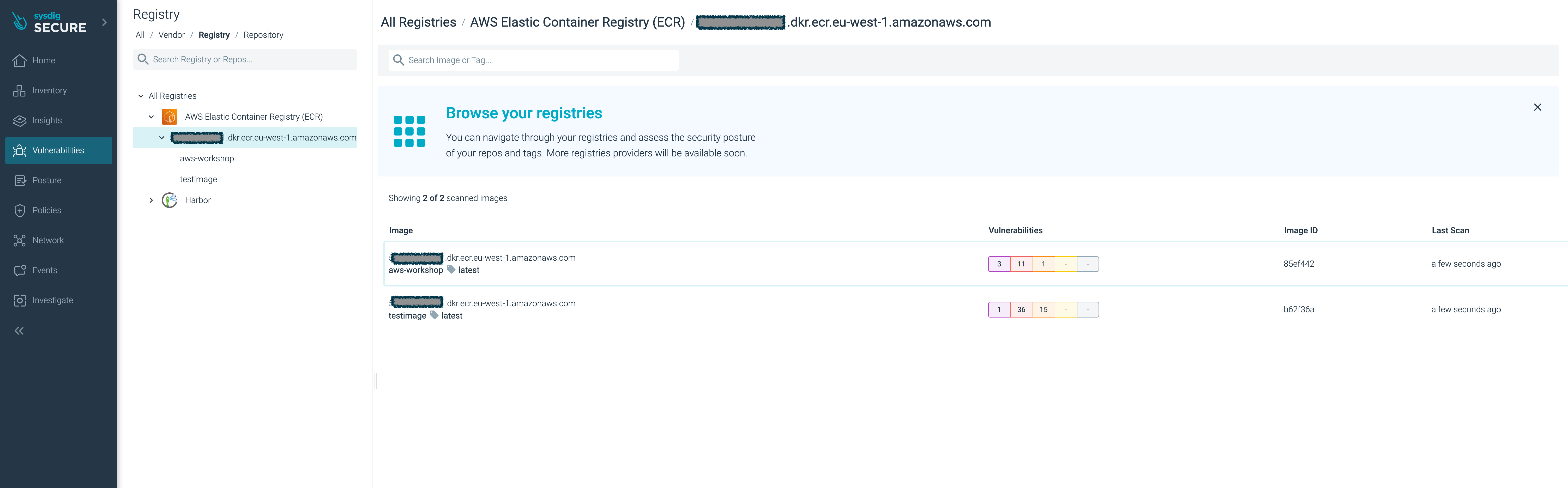
Click your new
aws-workshopimage.You’ll see the image have several major vulnerabilities.
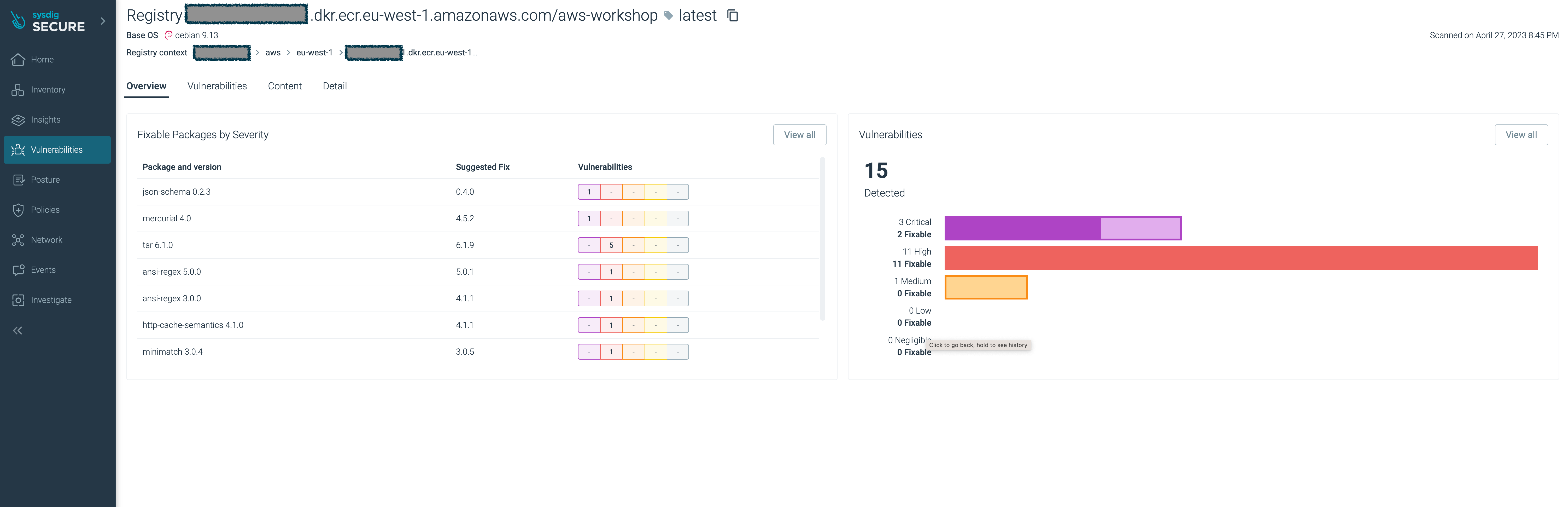
With Sysdig Secure you have full visibility of the security and compliance posture across your entire estate, in a single pane of glass, and as a central location for all security profiles and policies.