Scan images from ECR
Now that our automated scanner is in place, it will trigger full registry scans periodically.
In this step, you are going to build a new image and push it to your registry.
Then, you’ll trigger a manual scan outside of the normal schedule.
Download Example Dockerfile and Sources
Go to your Cloud9 Workspace and download and uncompress example container files:
wget https://github.com/johnfitzpatrick/hello-world-node-vulnerable/archive/v1.2.zip unzip v1.2.zip cd hello-world-node-vulnerable-1.2To illustrate the images scanning process, build the example Node.JS application (based on the official “hello world” example described in their website). Then, build and push the image to ECR with:
export ECR_NAME=aws-workshop export REGION=us-east-1 export AWS_ACCOUNT=$(aws sts get-caller-identity | jq '.Account' | xargs) export IMAGE=$AWS_ACCOUNT.dkr.ecr.$REGION.amazonaws.com/$ECR_NAME docker build . -t $IMAGE docker push $IMAGE(If you face an unauthenticated error go to your AWS console UI, Amazon ECR > Repositories, open previously created “aws-workshop” repository, click on “View push commands” button, copy the authentication string, and execute it in your terminal. After that you can retry previous step).
Trigger the manual scan
Lets trigger a manual scan (we don’t want to wait until the cron job triggers next scan action). Launch a job instance using kubectl:
kubectl create job --from=cronjob/registry-scanner registry-scanner-manual
The job creates a pod in the default namespace to retrieve the list of images and scan them one by one. Logs from the pod can be checked to see if everything went fine.
kubectl get po
Take note of pod name, it should be something like registry-scanner-manual-. This pod will also create a second pod (worker pod) if it detects images matching scan requirements like creation date, etc.
NAME READY STATUS RESTARTS AGE
registry-scanner-manual-lncqq 1/1 Running 0 13s
registry-scanner-worker-tt5ck-1-hts85 0/1 Completed 0 11s
Retrieve pod logs with kubectl:
kubectl logs registry-scanner-manual-lncqq
Logs should clarify if the scan action where successful. All images within the ECR repository should have been scanned.
...
...
{"level":"info","component":"report-builder","time":"2023-04-25T09:55:23Z","message":"Registry image scan has finished. Total: 1 = Success: 1 + Failed: 0 + Skipped: 0"}
Review Scan Results on Sysdig Secure Dashboard
To see the scan results on Sysdig Secure Dashboard:
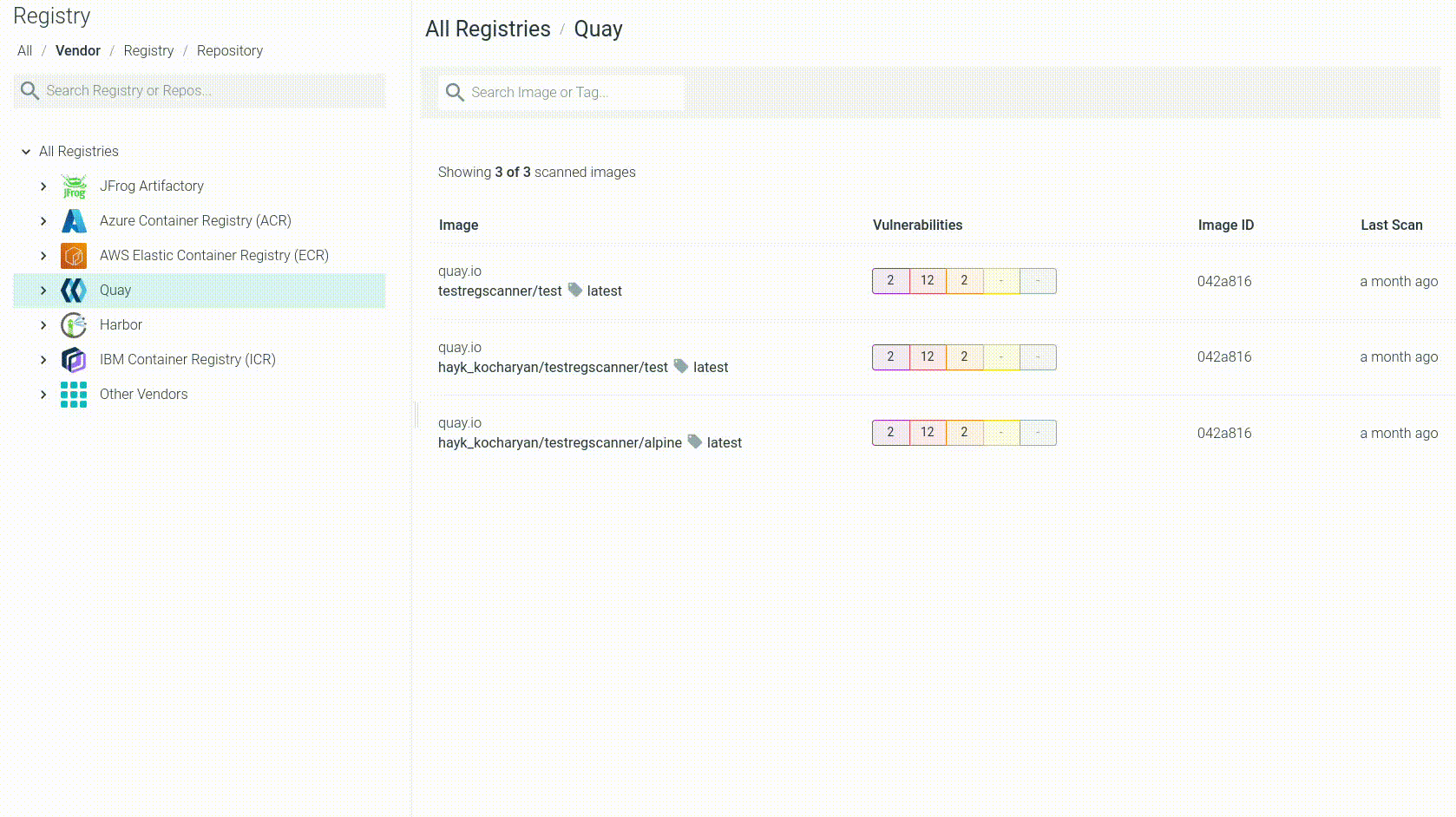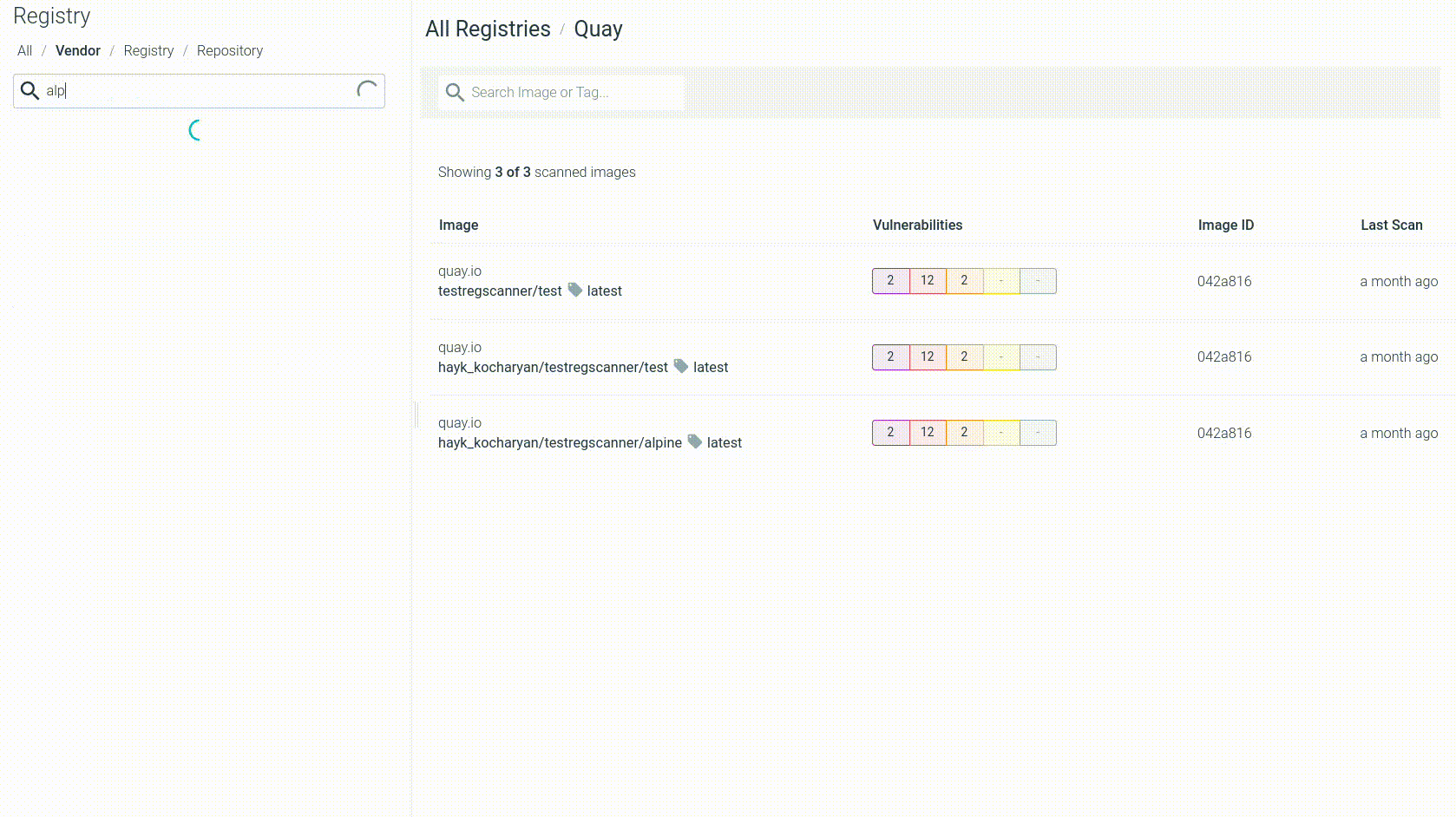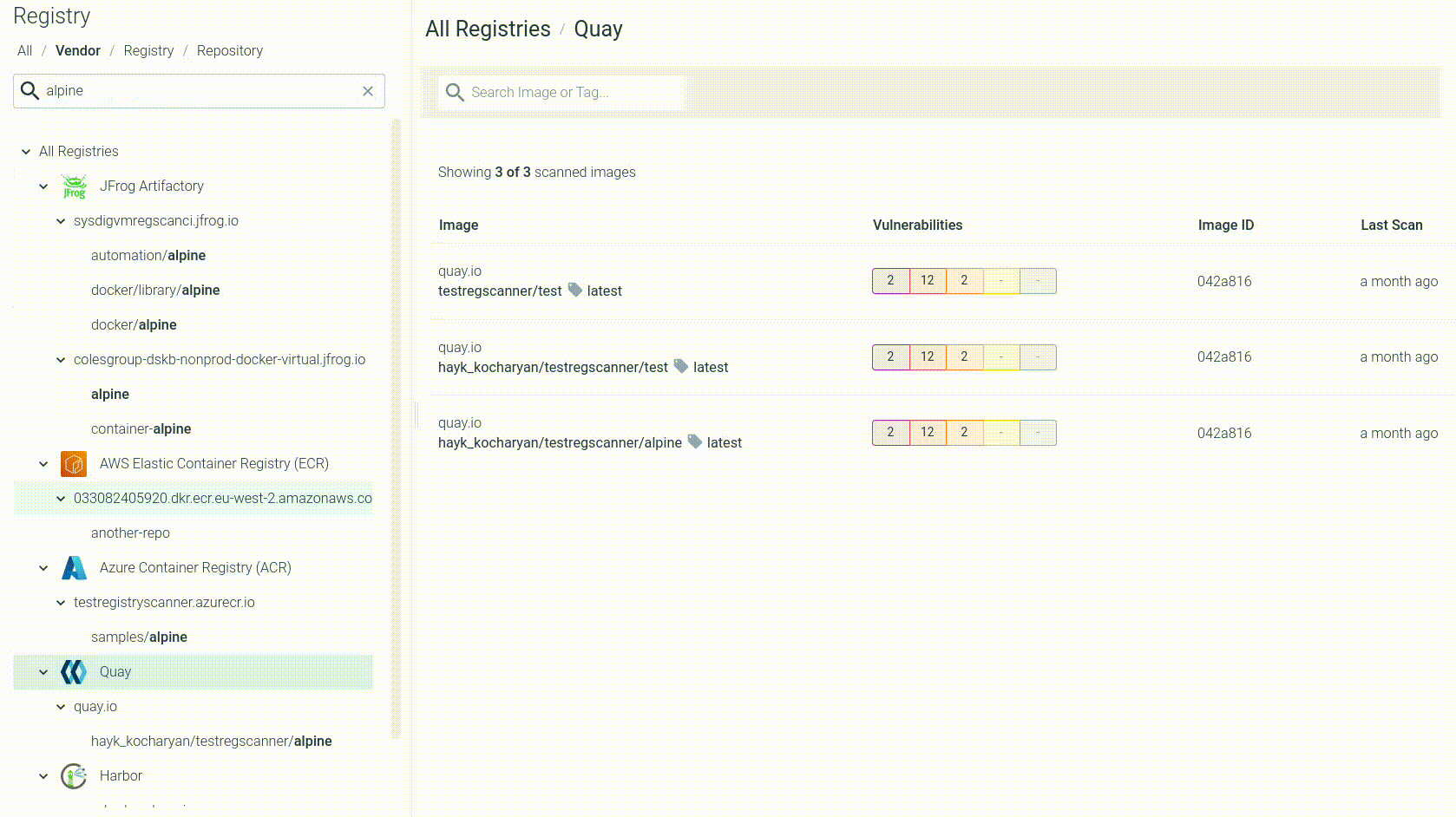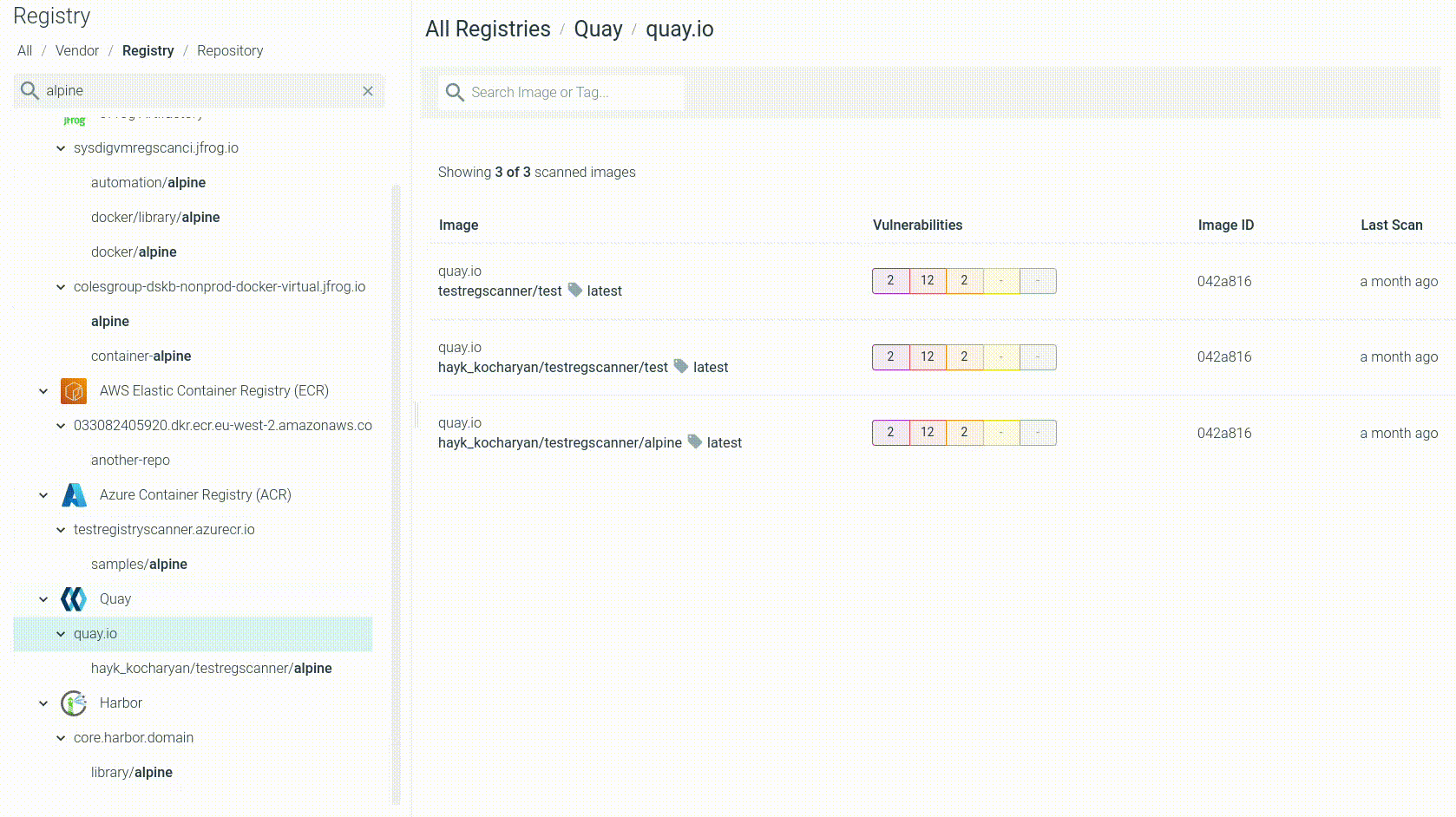
Log into the Sysdig Secure UI, and browse to Vulnerabilities > Registry:
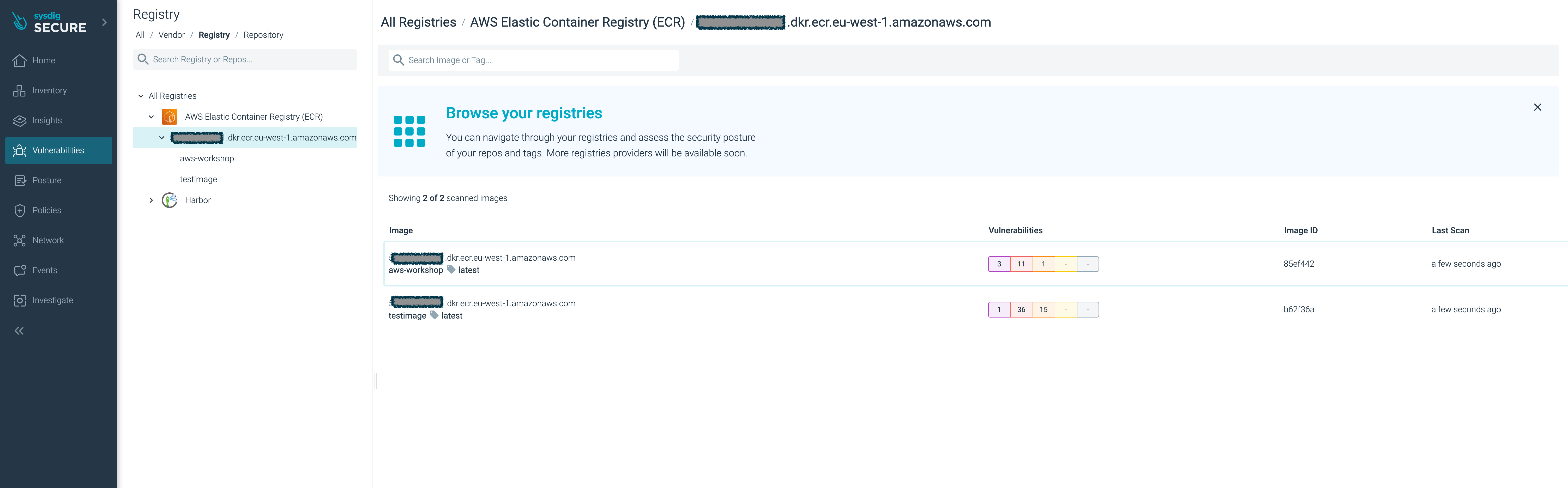
Click your new
aws-workshopimage.You’ll see the image have several major vulnerabilities.
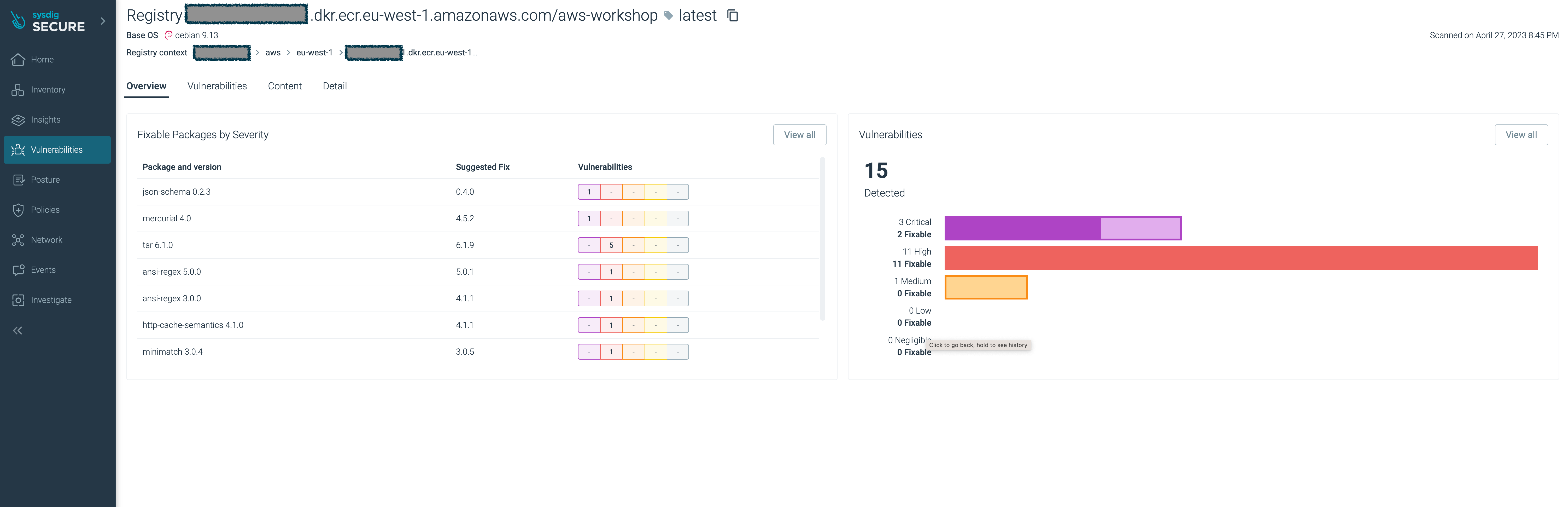
With Sysdig Secure you have full visibility of the security and compliance posture across your entire estate, in a single pane of glass, and as a central location for all security profiles and policies.