Now you are going to deploy a new instrumented task in Fargate. To do so, you are going to create a new CloudFormation Template (CFT).
Review the CFT provided at the bottom of this page before you deploy it. It uses the sysdiglabs/writer-to-bin image. This app just writes under bin. Once this workload is instrumented and deployed, this simple action will be detected by the agent Runtime Detection engine and will trigger an event in Sysdig Secure.
The policy detecting this event (Suspicious Filesystem Changes) is enabled by default. Explore other security policies and rules and learn how can you modify them to fit your security needs. After this little practice, it might be a good idea to take one of your applications deployed in Fargate and instrument it following this steps. Then, go to Sysdig Secure and observe which policies and rulescan be applied to your particular use-case.
Deploying and instrumenting a CFT
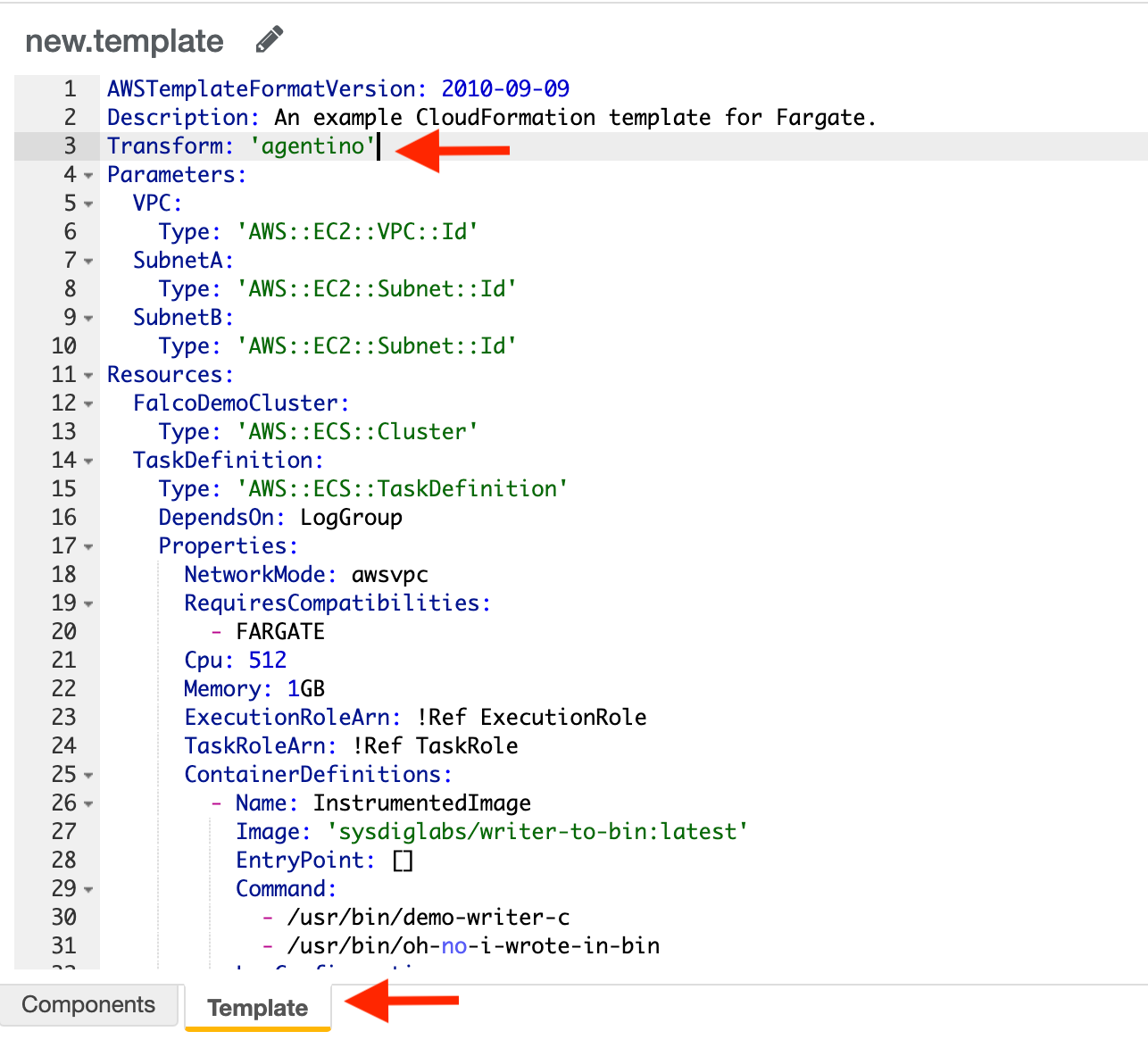
- First, instrument your template. To do so, copy the output of the previous step (
Transform: <macro-name>) at root level of the template like the following example (remember that you can use the CF Template provided at the bottom of this page!):
AWSTemplateFormatVersion: 2010-09-09
Description: An example CloudFormation template for Fargate.
Transform: agentino
Parameters:
VPC:
Type: AWS::EC2::VPC::Id
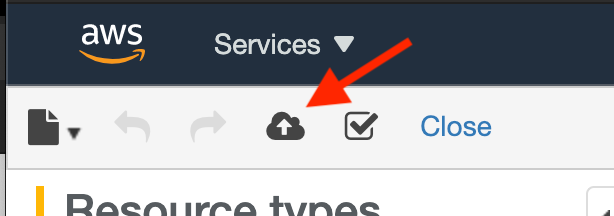
Go to Create Stack CloudFormation form. Or go to CloudFormation and click on Create Stack.
Select Create template in Designer and click Create template in designer. From here, switch to the Template tab (bottom of the page) and copy your template (remember to instrument it as instructed).
Click on Create Stack (cloud icon). You will need to:
- Click on Next to the Specify stack details
- Name the task (for example, falcodemocluster)
- Select the VPC and subnets you created in the first step.
- Click Next two times until you get to the Review step.
- Select the required boxes to continue.
- Click on Create stack.
In a couple of minutes the task will be deployed.
Example CFT
Copy this template to create a new task in AWS Fargate. Remember to instrument it as explained above.
1AWSTemplateFormatVersion: 2010-09-09
2Description: An example CloudFormation template for Fargate.
3Parameters:
4 VPC:
5 Type: AWS::EC2::VPC::Id
6 SubnetA:
7 Type: AWS::EC2::Subnet::Id
8 SubnetB:
9 Type: AWS::EC2::Subnet::Id
10Resources:
11 FalcoDemoCluster:
12 Type: AWS::ECS::Cluster
13 TaskDefinition:
14 Type: AWS::ECS::TaskDefinition
15 # Makes sure the log group is created before it is used.
16 DependsOn: LogGroup
17 Properties:
18 # awsvpc is required for Fargate
19 NetworkMode: awsvpc
20 RequiresCompatibilities:
21 - FARGATE
22 # 256 (.25 vCPU) - Available memory values: 0.5GB, 1GB, 2GB
23 # 512 (.5 vCPU) - Available memory values: 1GB, 2GB, 3GB, 4GB
24 # 1024 (1 vCPU) - Available memory values: 2GB, 3GB, 4GB, 5GB, 6GB, 7GB, 8GB
25 # 2048 (2 vCPU) - Available memory values: Between 4GB and 16GB in 1GB increments
26 # 4096 (4 vCPU) - Available memory values: Between 8GB and 30GB in 1GB increments
27 Cpu: 512
28 # 0.5GB, 1GB, 2GB - Available cpu values: 256 (.25 vCPU)
29 # 1GB, 2GB, 3GB, 4GB - Available cpu values: 512 (.5 vCPU)
30 # 2GB, 3GB, 4GB, 5GB, 6GB, 7GB, 8GB - Available cpu values: 1024 (1 vCPU)
31 # Between 4GB and 16GB in 1GB increments - Available cpu values: 2048 (2 vCPU)
32 # Between 8GB and 30GB in 1GB increments - Available cpu values: 4096 (4 vCPU)
33 Memory: 1GB
34 # A role needed by ECS.
35 # "The ARN of the task execution role that containers in this task can assume. All containers in this task are granted the permissions that are specified in this role."
36 # "There is an optional task execution IAM role that you can specify with Fargate to allow your Fargate tasks to make API calls to Amazon ECR."
37 ExecutionRoleArn: !Ref ExecutionRole
38 # "The Amazon Resource Name (ARN) of an AWS Identity and Access Management (IAM) role that grants containers in the task permission to call AWS APIs on your behalf."
39 TaskRoleArn: !Ref TaskRole
40 ContainerDefinitions:
41 - Name: InstrumentedImage
42 # Ref is not handled yet :(
43 Image: "sysdiglabs/writer-to-bin:latest"
44 # We override EntryPoint during rewrite so we MUST be explicit in the template
45 EntryPoint: []
46 Command: ["/usr/bin/demo-writer-c", "/usr/bin/oh-no-i-wrote-in-bin"]
47 # Send application logs to CloudWatch Logs
48 LogConfiguration:
49 LogDriver: awslogs
50 Options:
51 awslogs-region: !Ref AWS::Region
52 awslogs-group: !Ref LogGroup
53 awslogs-stream-prefix: ecs
54 # A role needed by ECS
55 ExecutionRole:
56 Type: AWS::IAM::Role
57 Properties:
58 AssumeRolePolicyDocument:
59 Statement:
60 - Effect: Allow
61 Principal:
62 Service: ecs-tasks.amazonaws.com
63 Action: 'sts:AssumeRole'
64 ManagedPolicyArns:
65 - 'arn:aws:iam::aws:policy/service-role/AmazonECSTaskExecutionRolePolicy'
66 # A role for the containers
67 TaskRole:
68 Type: AWS::IAM::Role
69 Properties:
70 AssumeRolePolicyDocument:
71 Statement:
72 - Effect: Allow
73 Principal:
74 Service: ecs-tasks.amazonaws.com
75 Action: 'sts:AssumeRole'
76 # ManagedPolicyArns:
77 # -
78 Policies:
79 - PolicyName: root
80 PolicyDocument:
81 Version: 2012-10-17
82 Statement:
83 # Needed for creating log group for falco
84 - Effect: Allow
85 Action: "cloudwatch:*"
86 Resource: "*"
87 # Permissions given in the default iam role for ecs tasks
88 - Effect: Allow
89 Action:
90 - "ecr:GetAuthorizationToken"
91 - "ecr:BatchCheckLayerAvailability"
92 - "ecr:GetDownloadUrlForLayer"
93 - "ecr:BatchGetImage"
94 - "logs:CreateLogGroup"
95 - "logs:CreateLogStream"
96 - "logs:PutLogEvents"
97 Resource: "*"
98 ContainerSecurityGroup: # aka no security group
99 Type: AWS::EC2::SecurityGroup
100 Properties:
101 GroupDescription: TEST ONLY
102 VpcId: !Ref VPC
103 SecurityGroupIngress:
104 - IpProtocol: tcp
105 FromPort: 0
106 ToPort: 65535
107 CidrIp: 0.0.0.0/0
108 Service:
109 Type: AWS::ECS::Service
110 Properties:
111 ServiceName: SDSDemoSvc
112 Cluster: !Ref FalcoDemoCluster
113 TaskDefinition: !Ref TaskDefinition
114 DeploymentConfiguration:
115 MinimumHealthyPercent: 100
116 MaximumPercent: 200
117 DesiredCount: 1
118 LaunchType: FARGATE
119 # This is required otherwise we do not get SYS_PTRACE :(
120 PlatformVersion: 1.4.0
121 NetworkConfiguration:
122 AwsvpcConfiguration:
123 AssignPublicIp: ENABLED
124 Subnets:
125 - !Ref SubnetA
126 - !Ref SubnetB
127 SecurityGroups:
128 - !Ref ContainerSecurityGroup
129 LogGroup:
130 Type: AWS::Logs::LogGroup