Sysdig Secure uses Falco under the hood to deliver Runtime Security for Linux, containers and Kubernetes.
Hence, all the benefits of the Open Source Ecosystem are available when protecting workloads in runtime.
In this module you will learn how to detect and respond to runtime security threats.
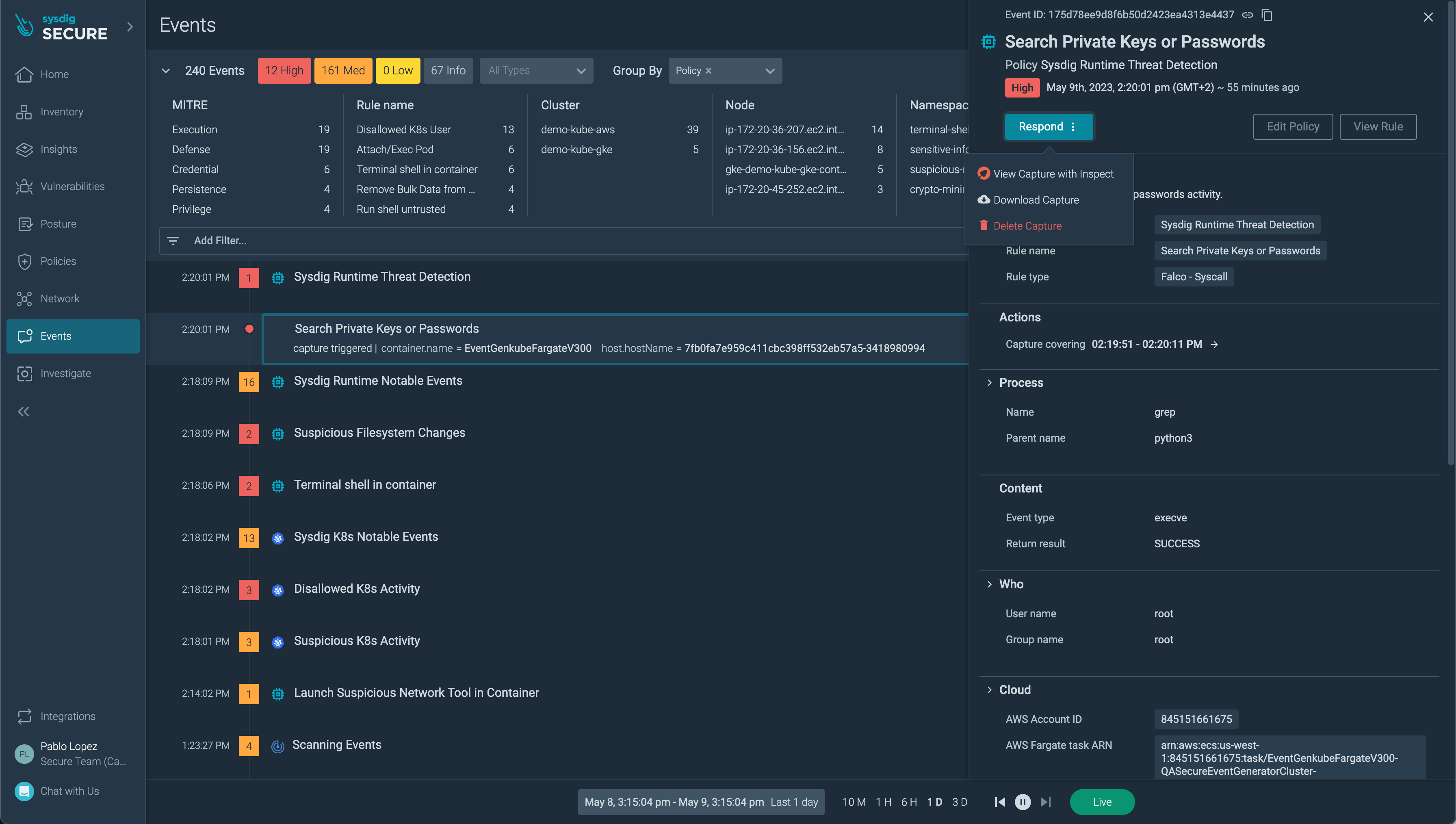
Events
Events are the result of rules in a policy being triggered, hence they can be generated by syscall activity, but also from cloud events (previous sub-module). Browse to this section and observe some of the activity.
Enable Runtime Security policies and create a custom Policy
Visit your Sysdig Secure account to and check that all the Kubernetes Audit and Runtime (Workload) policies are enabled. If not, enable them in the Secure > Runtime Policies dashboard.
Generating threats
In the next section you will trigger some attack scenarios similar to real attacks.
- Malware library compromising our cluster
- Vulnerable workload being exploited
- Shell intrusion using stolen credentials
Reproducing more advanced attack patterns
To learn more about more advanced attack scenarios, visit the Sysdig Public training page.