Threat 1: Exploit vulnerability
Attack scenario 1: Vulnerable workload being exploited
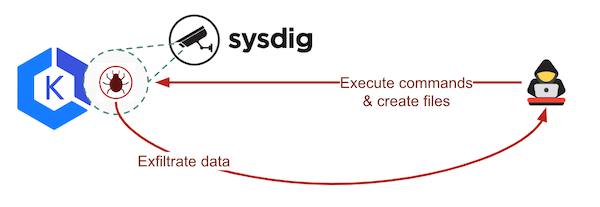
Scenario
A micro-services application requires several containers. One of them has an extremely dangerous zero-day vulnerability that no scanner on the market could detect. A hacker identifies the vulnerable image and start exploiting it, exfiltrating information, and writting and executing bad stuff.
Explanation
Security Playground acts as a vulnerable workload (it is a dumb application created by Sysdig for testing purposes), exposing some intentional backdoors that can trigger read/write operations.
Trigger
The script static/code/offensive/exploit-playground.sh will release the ‘attack’ through the EKS Load Balancer, injecting commands to be executed by the container.
Detection
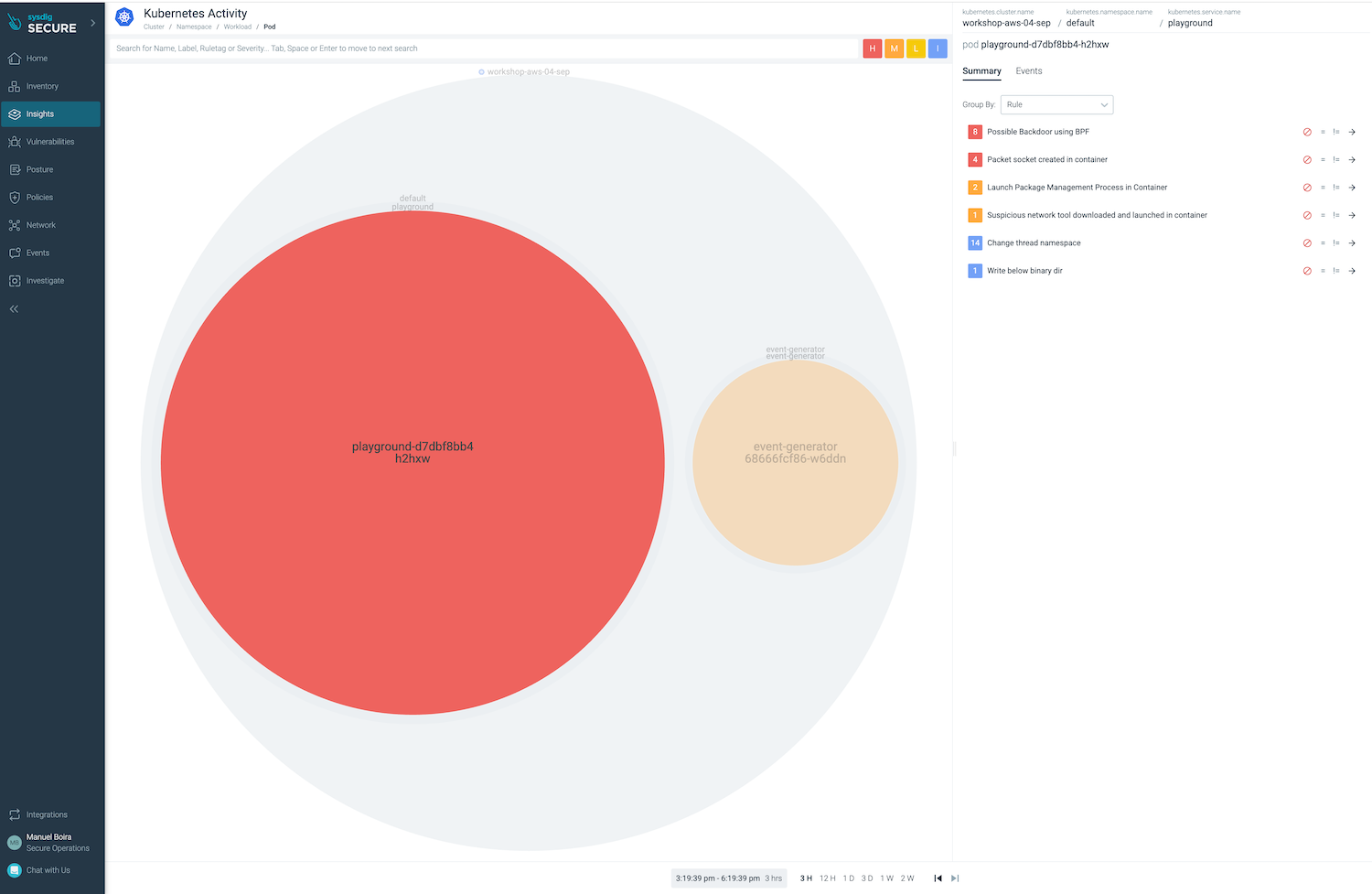
Browse to Insights > Kubernetes Activity to see how the events were captured. Click on the “playground” bubble to see more details about its events in the summary colum.
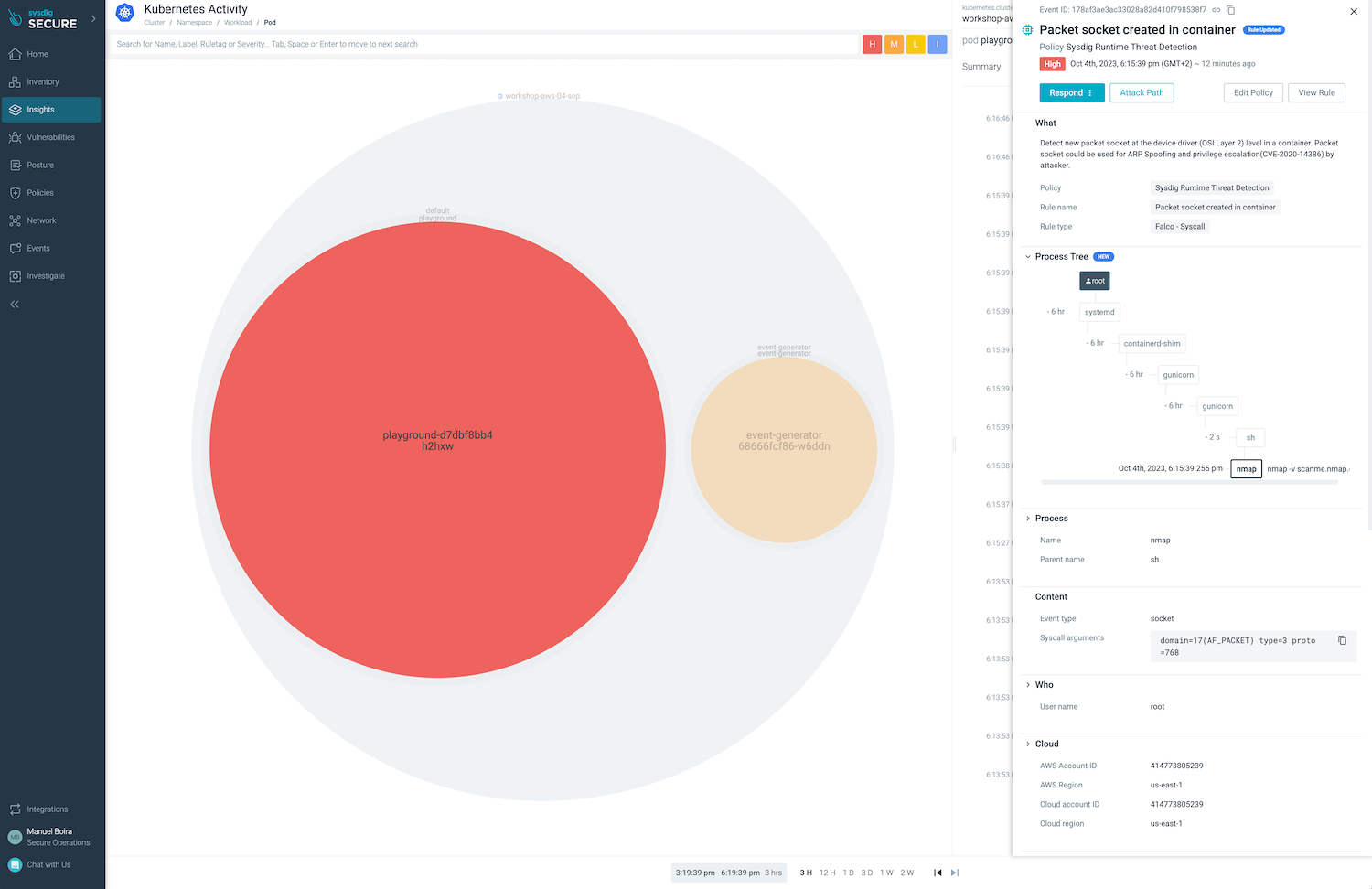
Click on the Events column on the top right side and expand one of the events to see it in context.
An alternative way to explore events is browsing to Events > Events Feed, extending a group of events and then one of the events.
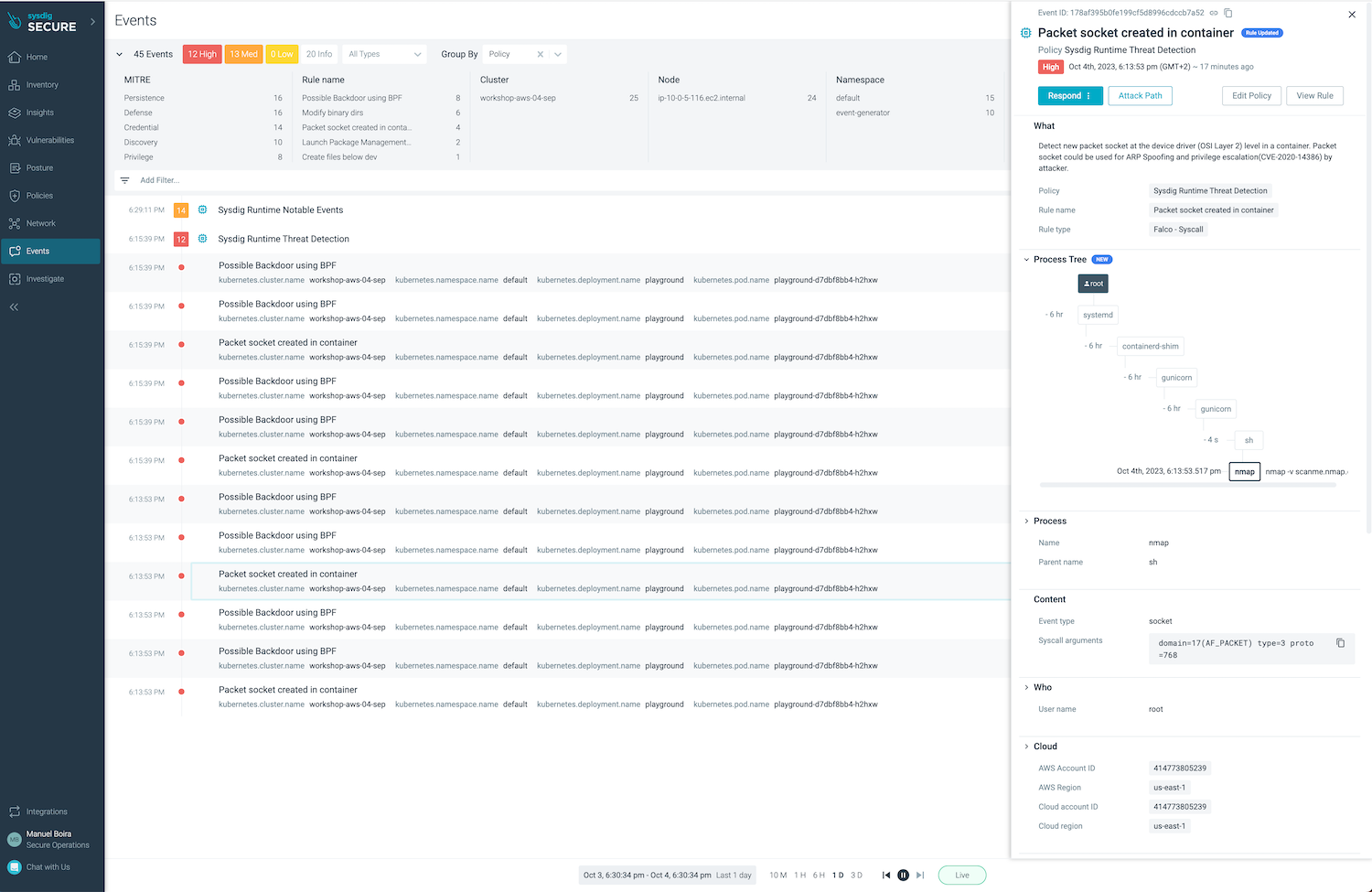
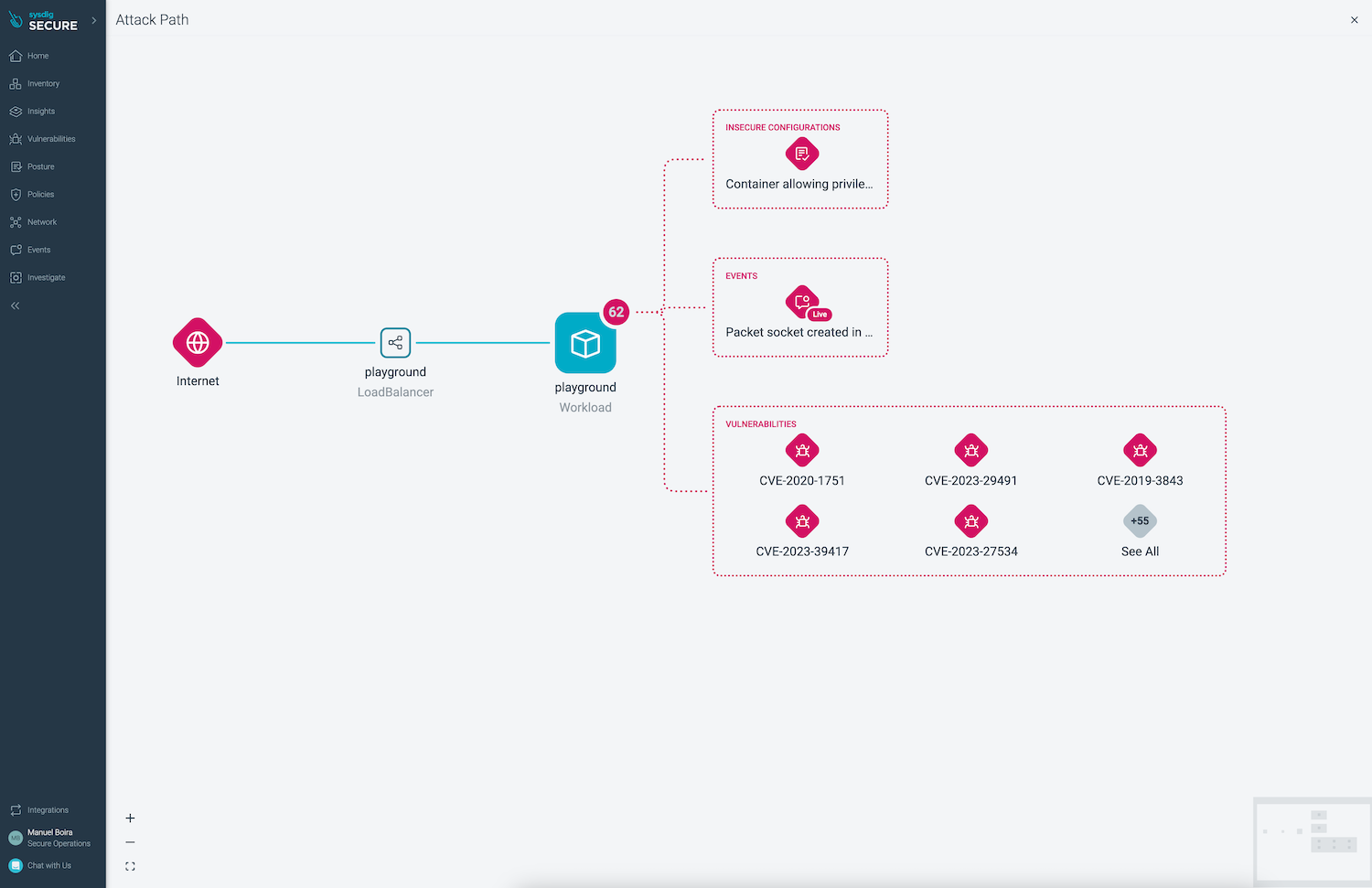
There are two interesting actions we can perform in order to improve our insight on what is happening: Attack Path, Audit Logs, Forensic analysis of captures.
a) Investigate Attack path (Attack path button) to get events, vulnerabilities and misconfigurations in context.
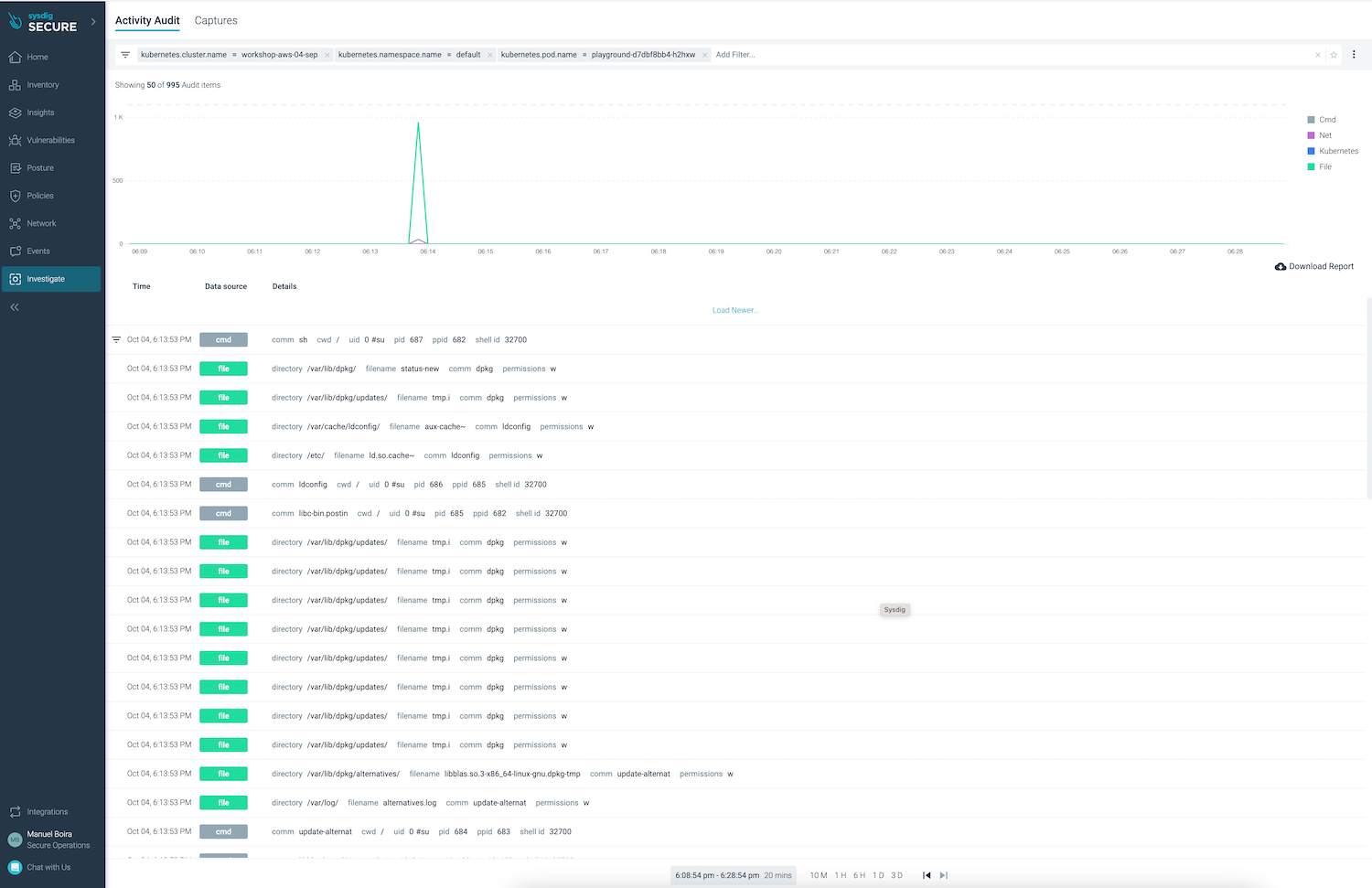
b) View Audit logs (Respond > View Audit logs) showing what happened within the container at that time.
c) Forensic analysis using Sysdig captures This option will be reviewed in the next scenarios.