Threat 2: Malware library
Attack scenario 2: Malware library compromising our cluster
Scenario
A bad actor infiltrated into our CI pipeline injected malware packages into an image that has been deployed to production. After some time it starts triggering automated actions, attempting to compromise our system.
Explanation
Falco Event Generator has been deployed together with your EKS cluster. This workload generates activity in the cluster that might be an indicator of a compromised environment.
Trigger
No manual actions are required as Falco Event Generator is already running and trying to do bad things.
Detection
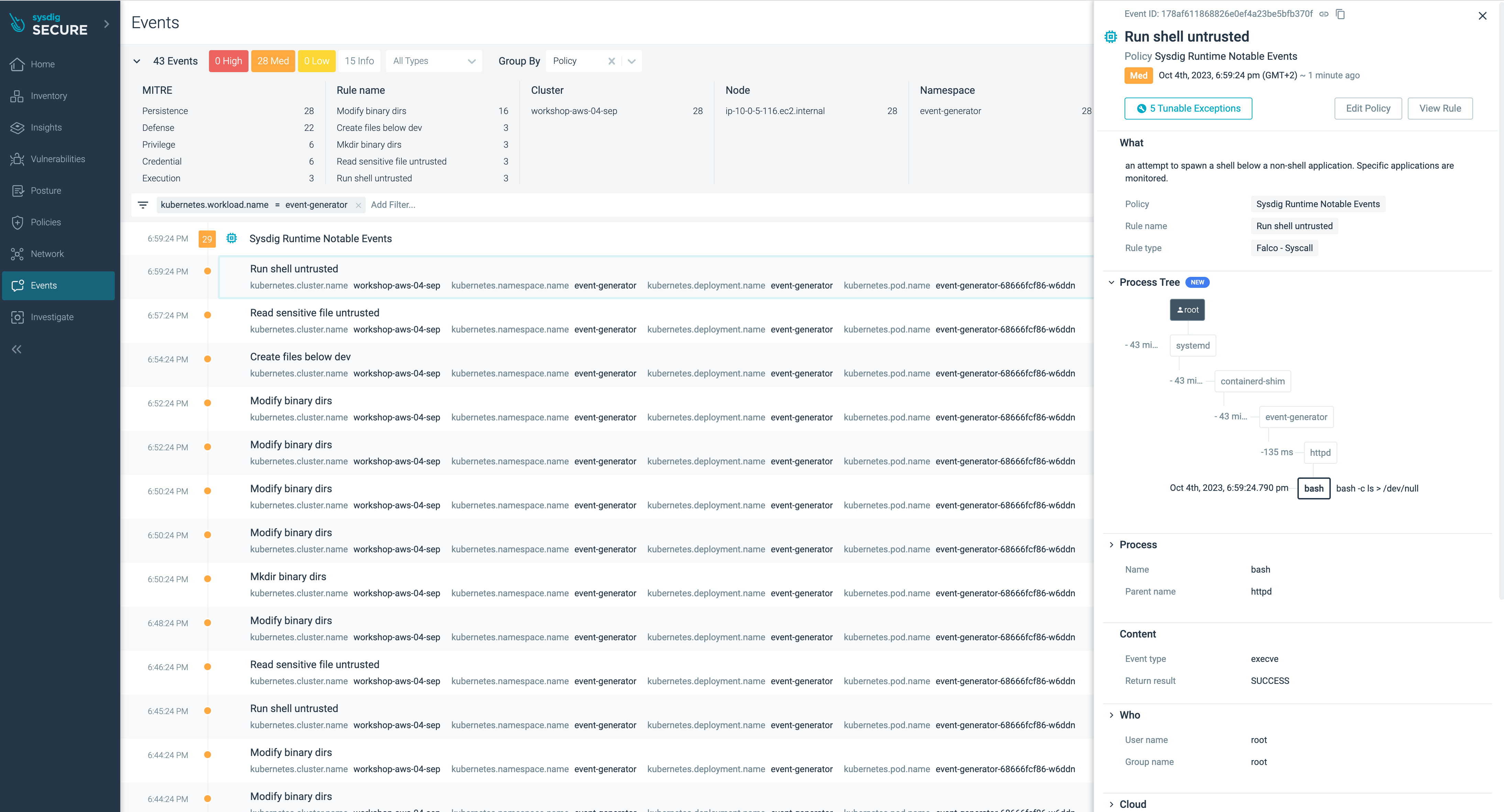
Let’s browse to Events > Events Feed and type in the Add Filter textbox kubernetes.workload.name = event.generator.
We can investigate now how the Pod event-generator is triggering actions, trying to find any weak point to escalate privileges, make lateral movements or exfiltrate information.