Install the Orchestrator
In this step you’ll be installing the Orchestrator Agent with CloudFormation.
This component is a collection point installed on each ECS cluster, and has two main functions. First, it collects data from the Sysdig Serverless Workload Agent, and sends them to the Sysdig backend. Second, it syncs the Falco runtime policies and rules to Sysdig Serverless Workload Agent from the Sysdig backend.
For this step, you will need some information from your Sysdig account. Visit the Get Started section in Sysdig Secure and from the Install the Agent tab copy them.:
- your Agent Access Key: Something like: d5ef7776-92eb-d0c2-4174-0727fc0981f3.
- and your Collector address. Something like: collector-static.sysdigcloud.com.
And now, follow the next steps:
A Sysdig orchestrator Agent CloudFormation blueprint is provided in the assets file below and in the course assets that you downloaded for this module.
Go to CloudFormation Create Stack form. Or go to CloudFormation in your AWS Console and click on Create Stack.
Select Create template in Designer and click Create template in designer. From here, switch to the Template tab (bottom of the Dashboard) and copy the orchestrator agent template replacing all the existing content.
Click on Create Stack (cloud icon with an up arrow inside). Then, you will need to:
Click on Next to the Specify stack details
Set a Name (for example,
<my_identifier>-agentone)Set Access Key and Collector with the value retrieved from your Sysdig account
Select the VPC and subnets where your tasks are running or will be running.
It is important to use the VPC and subnets that you created for this module. Please, do not use the existing ones for the previous EKS Module. They are identified by: <your_identifier>-fargate-{vpc|subnet}
Click Next until you get to the Review step
Scroll down to the bottom
Check the required boxes to continue.
And click on Create Stack.
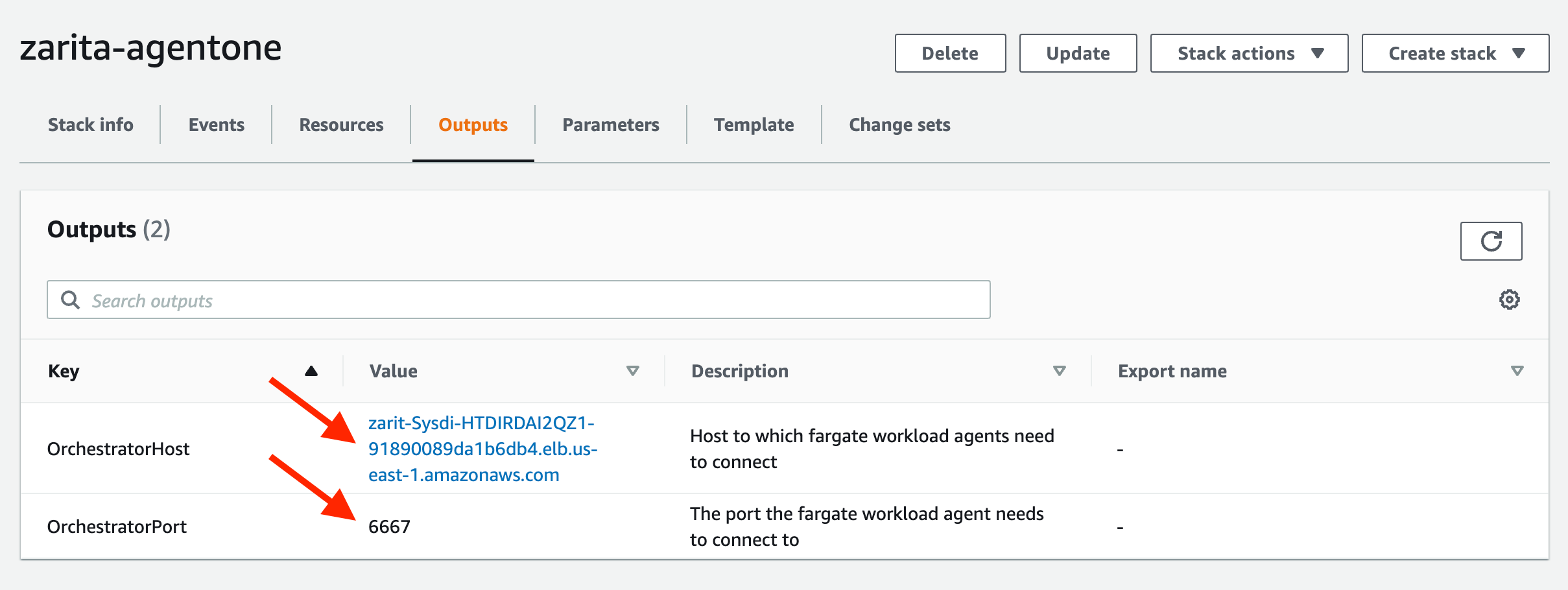
This action takes less than 10 minutes to be completed. Do not close this tab yet. Once that the stack creation is completed, go to Output and copy this two values:
- OrchestratorHost
- OrchestratorPort
This data will be required in the next step. While this is being prepared, you can preview a usage example of the tool:
Example of the values in Output tab:
Sysdig orchestrator Agent yaml
Just copy and paste this definition into the CloudFormation Template designer as explained above.
1AWSTemplateFormatVersion: 2010-09-09
2Description: Sysdig AWS support
3Metadata:
4 AWS::CloudFormation::Interface:
5 ParameterGroups:
6 - Label:
7 default: Sysdig Settings
8 Parameters:
9 - SysdigAccessKey
10 - SysdigCollectorHost
11 - SysdigCollectorPort
12 - Label:
13 default: Network Settings
14 Parameters:
15 - VPC
16 - SubnetA
17 - SubnetB
18 - Label:
19 default: Advanced Settings
20 Parameters:
21 - SysdigAgentTags
22 - SysdigOrchestratorAgentImage
23 - SysdigCheckCollectorCertificate
24 ParameterLabels:
25 VPC:
26 default: VPC Id
27 SubnetA:
28 default: Subnet A
29 SubnetB:
30 default: Subnet B
31 SysdigAccessKey:
32 default: Sysdig Access Key
33 SysdigCollectorHost:
34 default: Sysdig Collector Host
35 SysdigCollectorPort:
36 default: Sysdig Collector Port
37 SysdigAgentTags:
38 default: Agent Tags
39 SysdigOrchestratorAgentImage:
40 default: Sysdig Orchestrator Agent Image
41 SysdigCheckCollectorCertificate:
42 default: Check Collector SSL Certificate
43
44Parameters:
45 VPC:
46 Type: AWS::EC2::VPC::Id
47 Description: VPC where your service is deployed
48 SubnetA:
49 Type: AWS::EC2::Subnet::Id
50 Description: A subnet that can access internet and is reachable by instrumented services
51 SubnetB:
52 Type: AWS::EC2::Subnet::Id
53 Description: A subnet that can access internet and is reachable by instrumented services
54 SysdigAccessKey:
55 Type: String
56 SysdigOrchestratorAgentImage:
57 Type: String
58 Default: quay.io/sysdig/orchestrator-agent:latest
59 SysdigCollectorHost:
60 Type: String
61 Default: collector.sysdigcloud.com
62 SysdigCollectorPort:
63 Type: String
64 Default: "6443"
65 SysdigAgentTags:
66 Type: String
67 Description: Enter a comma-separated list of tags (eg. role:webserver,location:europe).
68 Default: ""
69 SysdigCheckCollectorCertificate:
70 Type: String
71 Default: "true"
72
73Outputs:
74 OrchestratorHost:
75 Description: Host to which fargate workload agents need to connect
76 Value: !GetAtt SysdigLoadBalancer.DNSName
77 OrchestratorPort:
78 Description: The port the fargate workload agent needs to connect to
79 Value: "6667"
80
81Resources:
82 SysdigAgentCluster:
83 Type: AWS::ECS::Cluster
84 Properties:
85 Tags:
86 - Key: application
87 Value: sysdig
88
89 SysdigOrchestratorAgentLogs:
90 Type: AWS::Logs::LogGroup
91
92 SysdigOrchestratorAgentExecutionRole:
93 Type: AWS::IAM::Role
94 Properties:
95 AssumeRolePolicyDocument:
96 Statement:
97 - Effect: Allow
98 Principal:
99 Service: ecs-tasks.amazonaws.com
100 Action: 'sts:AssumeRole'
101 ManagedPolicyArns:
102 - 'arn:aws:iam::aws:policy/service-role/AmazonECSTaskExecutionRolePolicy'
103 Tags:
104 - Key: application
105 Value: sysdig
106 SysdigOrchestratorAgentTaskRole:
107 Type: AWS::IAM::Role
108 Properties:
109 AssumeRolePolicyDocument:
110 Statement:
111 - Effect: Allow
112 Principal:
113 Service: ecs-tasks.amazonaws.com
114 Action: 'sts:AssumeRole'
115 # ManagedPolicyArns:
116 # -
117 Policies:
118 - PolicyName: root
119 PolicyDocument:
120 Version: 2012-10-17
121 Statement:
122 # Permissions given in the default iam role for ecs tasks
123 - Effect: Allow
124 Action:
125 - "ecr:GetAuthorizationToken"
126 - "ecr:BatchCheckLayerAvailability"
127 - "ecr:GetDownloadUrlForLayer"
128 - "ecr:BatchGetImage"
129 - "logs:CreateLogGroup"
130 - "logs:CreateLogStream"
131 - "logs:PutLogEvents"
132 Resource: "*"
133 Tags:
134 - Key: application
135 Value: sysdig
136 SysdigOrchestratorAgentSecurityGroup:
137 Type: AWS::EC2::SecurityGroup
138 Properties:
139 GroupDescription: Allow agentino to connect
140 VpcId: !Ref VPC
141 SecurityGroupIngress:
142 - IpProtocol: tcp
143 FromPort: 6667
144 ToPort: 6667
145 CidrIp: 0.0.0.0/0
146 Tags:
147 - Key: application
148 Value: sysdig
149 SysdigOrchestratorAgent:
150 Type: AWS::ECS::TaskDefinition
151 DependsOn: SysdigOrchestratorAgentLogs
152 Properties:
153 NetworkMode: awsvpc
154 RequiresCompatibilities:
155 - FARGATE
156 Cpu: 2048
157 Memory: 8GB
158 ExecutionRoleArn: !Ref SysdigOrchestratorAgentExecutionRole
159 TaskRoleArn: !Ref SysdigOrchestratorAgentTaskRole
160 ContainerDefinitions:
161 - Name: OrchestratorAgent
162 Image: !Ref SysdigOrchestratorAgentImage
163 Environment:
164 - Name: ACCESS_KEY
165 Value: !Ref SysdigAccessKey
166 - Name: COLLECTOR
167 Value: !Ref SysdigCollectorHost
168 - Name: COLLECTOR_PORT
169 Value: !Ref SysdigCollectorPort
170 - Name: TAGS
171 Value: !Ref SysdigAgentTags
172 - Name: CHECK_CERTIFICATE
173 Value: !Ref SysdigCheckCollectorCertificate
174 PortMappings:
175 - ContainerPort: 6667
176 LogConfiguration:
177 LogDriver: awslogs
178 Options:
179 awslogs-region: !Ref AWS::Region
180 awslogs-group: !Ref SysdigOrchestratorAgentLogs
181 awslogs-stream-prefix: ecs
182 Tags:
183 - Key: application
184 Value: sysdig
185
186 SysdigLoadBalancer:
187 Type: AWS::ElasticLoadBalancingV2::LoadBalancer
188 Properties:
189 IpAddressType: ipv4
190 Scheme: internal
191 Type: network
192 Subnets:
193 - !Ref SubnetA
194 - !Ref SubnetB
195 Tags:
196 - Key: application
197 Value: sysdig
198
199 SysdigTargetGroup:
200 Type: AWS::ElasticLoadBalancingV2::TargetGroup
201 Properties:
202 Port: 6667
203 Protocol: TCP
204 TargetType: ip
205 TargetGroupAttributes:
206 - Key: deregistration_delay.timeout_seconds
207 Value: 60 # default is 300
208 VpcId: !Ref VPC
209
210 SysdigLoadBalancerListener:
211 Type: AWS::ElasticLoadBalancingV2::Listener
212 Properties:
213 DefaultActions:
214 - TargetGroupArn: !Ref SysdigTargetGroup
215 Type: forward
216 LoadBalancerArn: !Ref SysdigLoadBalancer
217 Port: 6667
218 Protocol: TCP
219
220 SysdigOrchestratorAgentService:
221 Type: AWS::ECS::Service
222 DependsOn:
223 - SysdigLoadBalancerListener
224 Properties:
225 ServiceName: SysdigOrchestratorAgent
226 Cluster: !Ref SysdigAgentCluster
227 TaskDefinition: !Ref SysdigOrchestratorAgent
228 DeploymentConfiguration:
229 MinimumHealthyPercent: 100
230 MaximumPercent: 200
231 DesiredCount: 1
232 LaunchType: FARGATE
233 PlatformVersion: 1.4.0
234 NetworkConfiguration:
235 AwsvpcConfiguration:
236 AssignPublicIp: ENABLED
237 Subnets:
238 - !Ref SubnetA
239 - !Ref SubnetB
240 SecurityGroups:
241 - !Ref SysdigOrchestratorAgentSecurityGroup
242 LoadBalancers:
243 - ContainerName: OrchestratorAgent
244 ContainerPort: 6667
245 TargetGroupArn: !Ref SysdigTargetGroup
246 Tags:
247 - Key: application
248 Value: sysdig