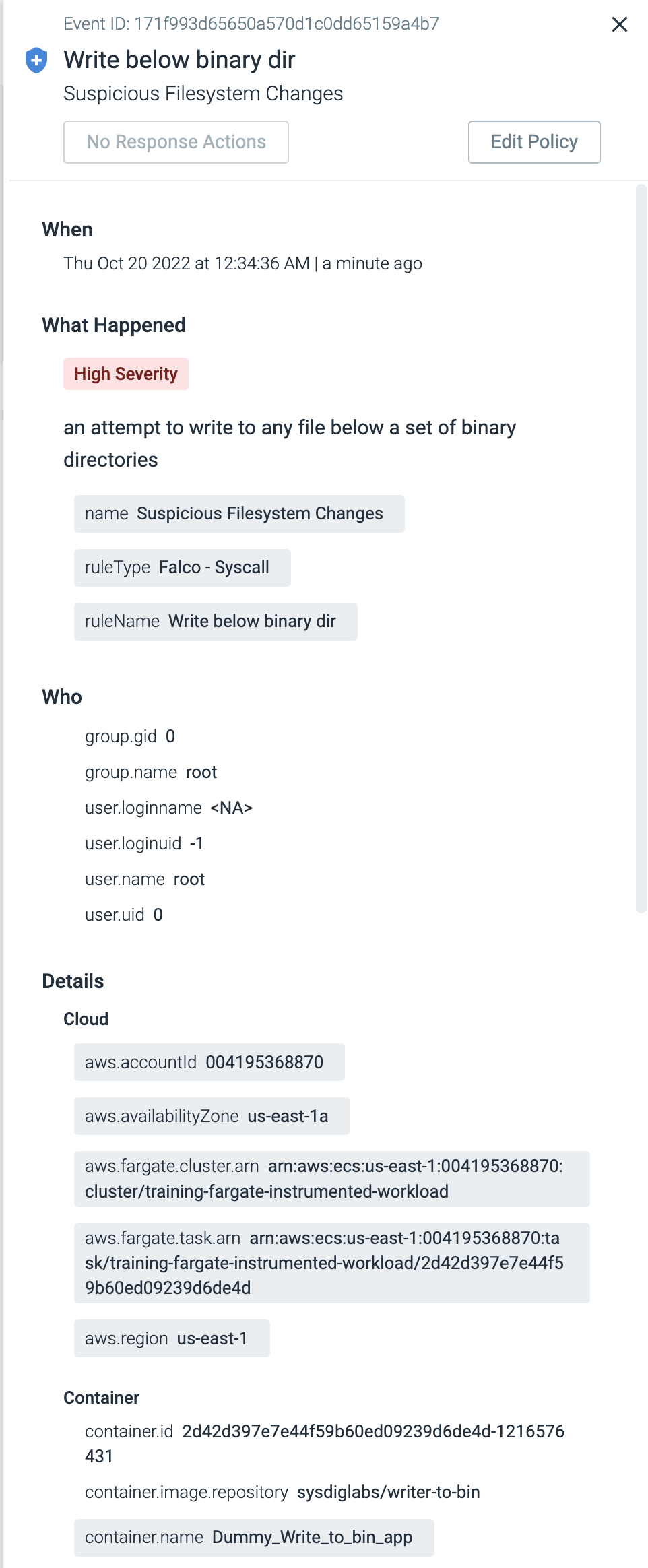
This application is writing under /bin, what is not a good practice. Luckily, by default you have a Falco Rule that detects this behaviour and a Sysdig Policy using this rule. So, you should get a notification out of the box.
Browse to Sysdig Secure > Events
Here you can find a feed with all the events that have ocurred during the last time period in your connected hosts. In this case, from your Fargate instance.

Select the triggered event and review in the lateral view all the information available.
From here you can visualize: = The policy and rule that was triggered by the event
- The Fargate instance identifier
- AWS Region
- Container name
- and much more!
You have finished this practice. Now you are ready to Detect Runtime security threats in your AWS Fargate workloads with Sysdig Secure.